Azure AD Integration
Azure AD Integration
Azure AD can be integrated via the OIDC integration.
Configure a new Azure AD App registration
Add a new Azure AD App registration
- From the
Azure Active Directory>App registrationsmenu, choose+ New registration - Enter a
Namefor the application (e.g.Kluctl Webui). - Specify who can use the application (e.g.
Accounts in this organizational directory only). - Enter Redirect URI (optional) as follows (replacing
my-kluctl-webui-urlwith your Kluctl Webui URL), then chooseAdd.- Platform:
Web - Redirect URI: https://
<my-kluctl-webui-url>/auth/callback
- Platform:
- When registration finishes, the Azure portal displays the app registration’s Overview pane. You see the Application (client) ID.
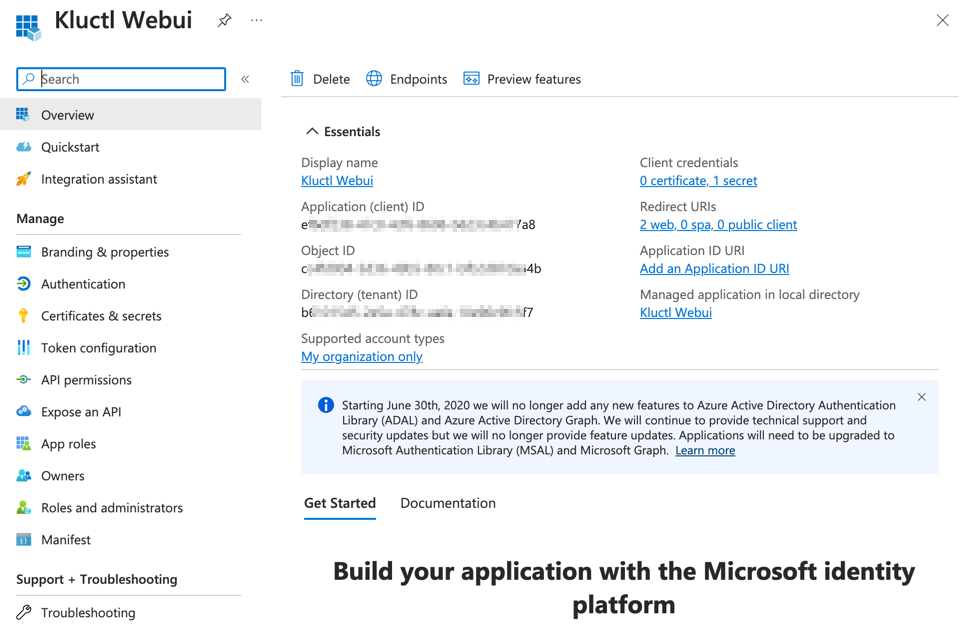
Add credentials a new Azure AD App registration
- From the
Certificates & secretsmenu, choose+ New client secret - Enter a
Namefor the secret (e.g.Kluctl Webui SSO).- Make sure to copy and save generated value. This is a value for the
oidc-client-secret.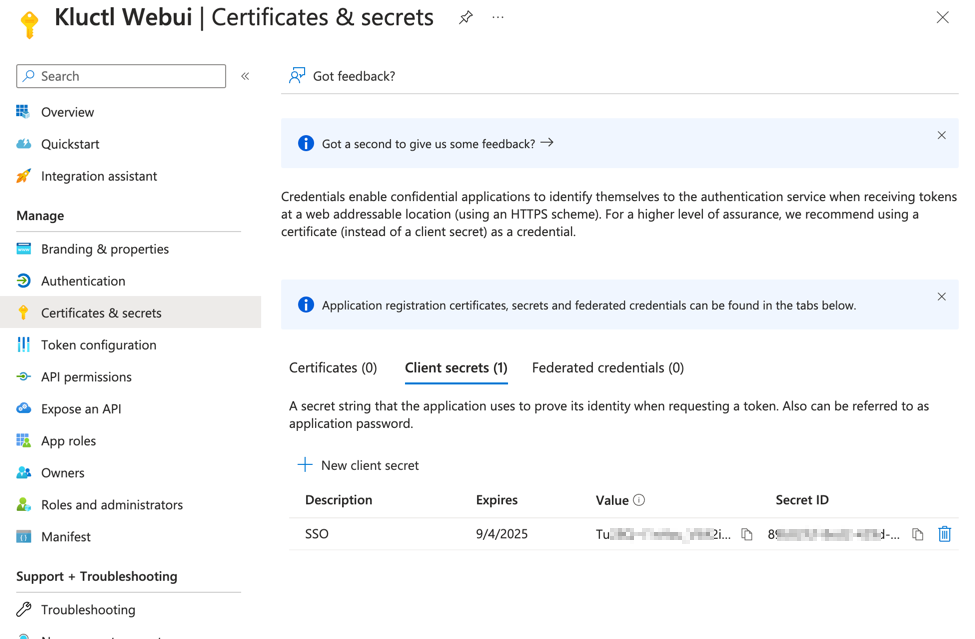
- Make sure to copy and save generated value. This is a value for the
Setup permissions for Azure AD Application
- From the
API permissionsmenu, choose+ Add a permission - Find
User.Readpermission (underMicrosoft Graph) and grant it to the created application: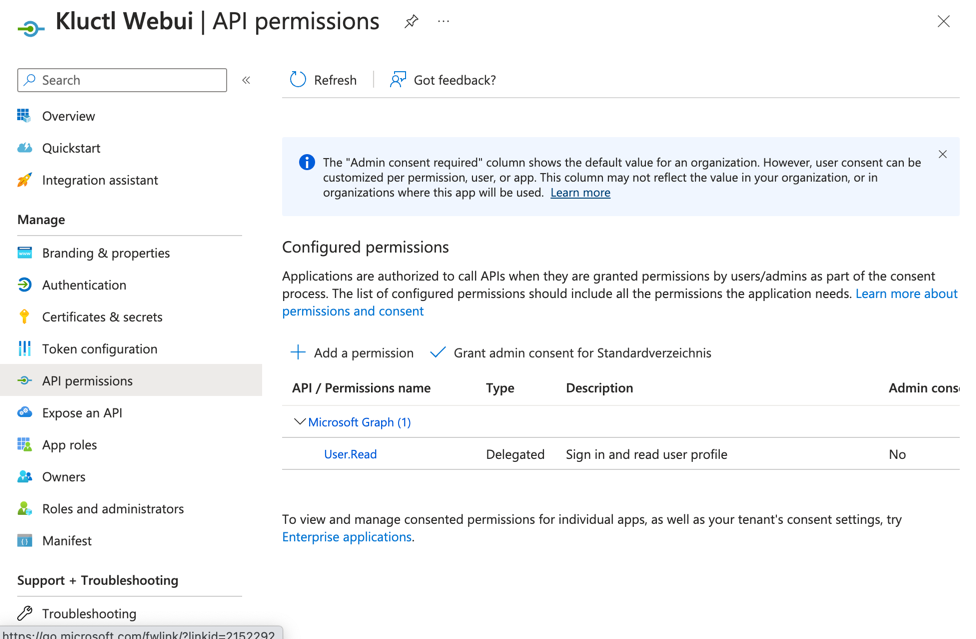
- From the
Token Configurationmenu, choose+ Add groups claim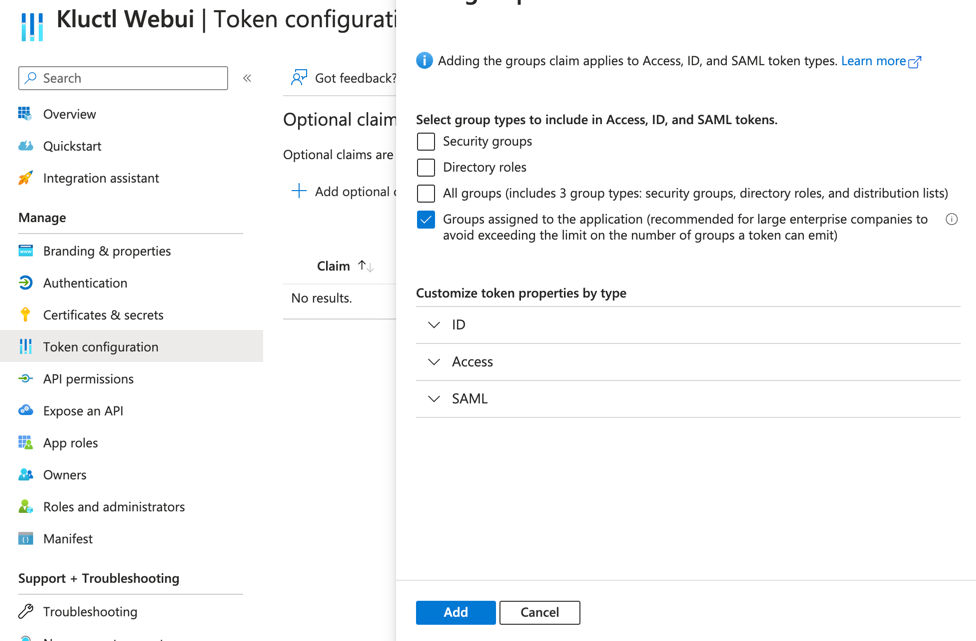
Associate an Azure AD group to your Azure AD App registration
- From the
Azure Active Directory>Enterprise applicationsmenu, search the App that you created (e.g.Kluctl Webui).- An Enterprise application with the same name of the Azure AD App registration is created when you add a new Azure AD App registration.
- From the
Users and groupsmenu of the app, add any users or groups requiring access to the service.
Configure the Kluctl Webui to use the new Azure AD App registration
Use the following configuration when installing the Webui. Replace occurrences of
<directory_tenant_id>, <client_id>, <my-kluctl-webui-url> and <admin_group_id> with the appropriate values from
above.
deployments:
- path: secrets
- git:
url: https://github.com/kluctl/kluctl.git
subDir: install/webui
ref:
tag: v2.26.0
vars:
- values:
args:
webui_args:
- --auth-oidc-issuer-url=https://login.microsoftonline.com/<directory_tenant_id>/v2.0
- --auth-oidc-client-id=<client_id>
- --auth-oidc-scope=openid
- --auth-oidc-scope=profile
- --auth-oidc-scope=email
- --auth-oidc-redirect-url=https://<my-kluctl-webui-url>/auth/callback
- --auth-oidc-group-claim=groups
- --auth-oidc-admins-group=<admin_group_id>
Also, add webui-secrets.yaml inside the secrets subdirectory:
apiVersion: v1
kind: Secret
metadata:
name: webui-secret
namespace: kluctl-system
stringData:
oidc-client-secret: "<client_secret>"
Please note that the client secret is sensitive data and should not be added unencrypted to you git repository. Consider encrypting it via SOPS.